Understanding MD5 Hashes and Security
Geek confession here. Before today I had a sorry understanding of what MD5 hashes were, and how they related to passwords and online security.
All I knew was they had something to do with obscuring your password so it could’t be cracked. Or something.
But after skimming a fascinating article on Ars Technica called How I became a password hacker I decided that ignorance was no longer an option.
So it turns out an MD5 is just a specific type of “cryptographic hash function“, which means it’s a one-way function; you can’t figure out what went into it just by looking at what came out of it. Badass.
This graphic (via Wikipedia) sums it up pretty nicely. (The “Input” represents a password, and the “Digest” represents a hash.)
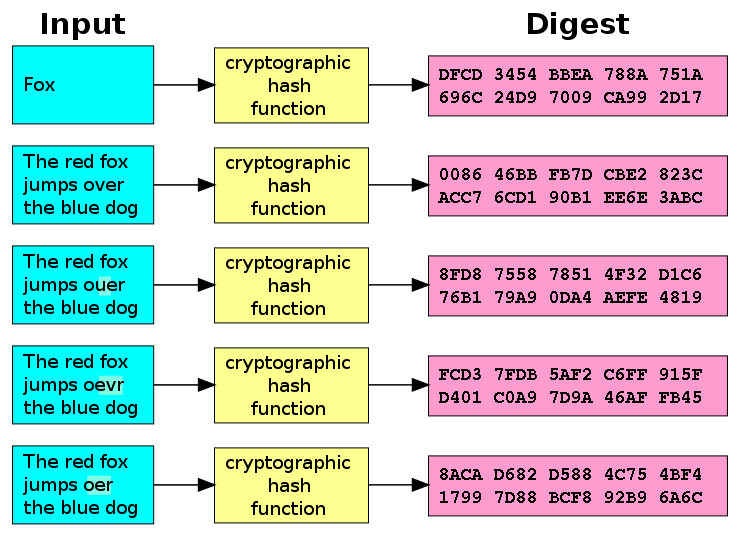
It turns out you can make MD5s yourself pretty easily. Do something like this on your command line (or you can just Google for “MD5 Generator”), and you can start to play around with making hashes. You’ll see that no matter what you use as your input, you get 32 characters of crap:
$ echo -n “hello world” | md5
$ 5eb63bbbe01eeed093cb22bb8f5acdc3
$ echo -n “helloooooooooooo world!” | md5
$ 9fa764163c098ec3374ef0c3f7419524
So again, that’s the secret. The magic is the crap. Those 32 characters are so crappy and so random, no amount of computing power can reverse-engineer it back into your password. And the other crucial piece of the pie: Your password is the only piece of input that will consistently produce that exact same piece of crap.
So how does this relate to passwords and security? Reading this blurb on the Wikipedia page made it all click for me:
Alice poses a tough math problem to Bob and claims she has solved it. Bob would like to try it himself, but would yet like to be sure that Alice is not bluffing. Therefore, Alice writes down her solution, computes its hash and tells Bob the hash value (whilst keeping the solution secret). Then, when Bob comes up with the solution himself a few days later, Alice can prove that she had the solution earlier by revealing it and having Bob hash it and check that it matches the hash value given to him before.
So that’s basically the gist of it. Pretty cool, and that ain’t no shit.